Eds First Report: Hacking 101 Part One:
Protecting yourself and getting your hacker game-face on.
By the end of this article you should have the knowledge to keep Cigna out of your data, pollute what data they have. Finally you will have the ability to do what you need to on the 'net while keeping your tracks hidden. All you need is open source software from the 'net and a little know-how..
Woohoo everyone!
This is Edward Tivrusky IV but you can call me Ed or by my nom de geurre, "Radical Edward". I work on the team that is defending Jeff Cobb from the bullies at Cigna insurance company. Everyone else has their own stuff to do and my stuff to do is investigations and data tracking. Not everything I do here is something that you can do where you are but there is a lot that the average person can do if they have the means and will to do it. I can help give you the means but you will have the supply the will for yourself. You must each decide how far to go and what to do; no moral judgments here. This is a tactical, technical guide. This is part one of my instant hacker series; part two will show you how to use the skills you learn here to get some things done to help any negotiations with Cigna.
Protecting Yourself First.
I will not be showing any mad hacker skillz here; I was asked to show you what you can do for yourself with just the computer that you have in your hands. There *are* things you can do if you do not live in the USA but we can save that for another time. If you want to practice being a movie-hacker, have fun!
There are two kinds of information that we are going to talk about, yours and theirs. "Yours" is your personal information and "theirs" is the dirt on the bad guys. The guiding principle in any kind of information war is pretty simple:
- Protect your information. This means keeping your personal details out of the hands of the enemy. They have no business with it anyways and untrustworthy groups like this "Cigna" will do terrible things to you when they do get your info.
- Counter-intelligence. This means polluting the information about you with false and misleading stuff.
- Get their personal information and make sure the targets know it. Make them feel like they made you feel. Like Mrs. Cobb likes to say, "karma is a bitch".
Protecting yourself on-line.
The information that Cigna gets about you on-line is only used for one purpose: to try to cheat you out of money. No other reason. If it was for intimidation Cigna would tell you that they are doing it but most times you can only find out after the fact. Getting information like this isn't hard really; most people are sloppy about watching what they post and where. This works both for and against you. There is not a whole lot that you can do about what is already there but by following 3 simple rules you can take steps to take away any advantage that the enemy might have. Learn these well, my Padawan learners. As Brad at All-American Burger says....
- Immediately stop posting on-line. Anything, no matter how innocent can be turned against you. Did you totter out to the mailbox with your cane and get the mail? And then post about it? Cigna would try to use this as proof that you are not disabled. Now if you must post on the 'net, look at everything you post on Facebook, Google+, Twitter, etc very carefully. Once you limit your *actual* posts it is time for..
- Disinformation. For everything you post about something you might be doing, post something that is also impossible. For example, say you are confined to a wheelchair; post something about going hang-gliding, complete with pictures you got from Google. The purpose is to pollute the quality of what is on the net about you. If they try to use your activities to prove you are not disabled but you have posted so much stuff that is obviously made up, it will make what they do have seem less dependable. Make your stories as wild as possible; have fun with it.
- Hide your tracks. It does little good to hide your data if you are just traipsing around the 'net leaving your signature behind. This isn't like in the movies where the evil hacker "bounces his signal all over the world" making it impossible for the good guys to track him. This has got to be the most invincibly stupid thing ever put into a movie. Not only is that how every connection on the 'net works anyway but *anyone* can trace that path back to the user in about 4 seconds with a single command. If you need to accomplish things on the 'net with relative anonymity, you can use what is called an "onion router". For a full explanation see the Wikipedia article but here is a summary:
Onion routing (OR) is a technique for anonymous communication over a computer network. Messages are repeatedly encrypted and then sent through several network nodes called onion routers. Like someone peeling an onion, each onion router removes a layer of encryption to uncover routing instructions, and sends the message to the next router where this is repeated. This prevents these intermediary nodes from knowing the origin, destination, and contents of the message.
The short answer is, this will keep anyone from tracking what you are doing which will be really important in the next part about doing your own background investigations (for entertainment purposes). So how can you too use this kind of power? Somewhat easily. There is an open source software project called TOR (The Onion Router) that has software for Windows, Mac, Linux, Android and who
What this software does is (basically) routes your 'net connection through a series of anonymous servers, triple encrypting and decrypting it along the way so that when your connection does complete, nobody on the receiving end has a clue where it came from.
What this might look like to you is this. If you open a browser and enter www.google.com, you will get the search engine you are used to seeing...in English. Now if you were to do the same thing only with The Onion Router in play on your PC, Google will almost certainly think you are coming to that site from somewhere in Europe or Asia and return results in that language. The OR expires connections every so often (4 hours I think) so if you connect at noon you might seem to be connecting from somewhere in the UK and if you do it again at dinner time it could say Germany or France or...you get the idea.
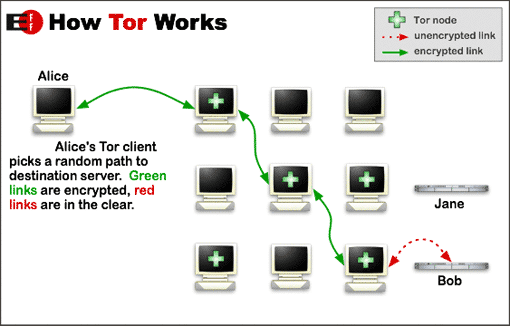 |
| Blatantly borrowed from the Wikipedia TOR article! |
The key things remaining to be controlled are the network end-clients: your browser, email, etc. Most browsers can be secured but are not by default; it leaves behind keys to tell some nosy bastard what your computer is running, software you are running and worse, sometimes they can be tricked into trying to auto-log you into a site using JavaScript (the programming language that runs in browsers and is used almost everywhere). So to make yourself really secure, check out the TOR Browser Project. It is simply a big fat software bundle that you can just download, unpack and run. It will automatically set up the TOR network connection and launch a special armored locked-down web browser. Now, anything you do through this tool is almost totally safe.
"Wait, almost safe? WTF?" I can hear it now and that's cool bro. The only thing left to cover is the crap that a (any) web browser leaves behind on your hard drive. Cookies from where you have been, browsing history, bookmarks, etc. If your laptop/desktop were ever to be seized (a real problem for some) then you are still busted after covering yourself so well. Not to worry mate; this is where we swing for the security fence!
The way to plug this hole is a trick hackers and computer-wise people have been doing for years and that is to boot an alternate operating system from a USB key (or other similar storage). This is kind of like having a second PC on your keyring. When you boot such a system you have a desktop, mouse, etc only anything you run will store stuff (if at all) on the USB key. When you are done using such a system, just unplug the USB key, stick it in your pocket and reboot. Now your old system is there just fine but all evidence of anything that you might have done is on the USB key, safe in your pocket. Your PC is clean.
Now what would really make this kick ass is if such a bootable key could also automagically handle the TOR routing management as well as having only a set of super-secure tools on board. This way you could just plug a key into a PC (ANY PC connected to the 'net of course), reboot it and have a custom, secure connection to do...anything. Sweet, eh? The good news is, such a thing exists and I have used it alot.
The Tails Project takes the TOR Browser project a bit further by making a special disk image that anyone can download and burn to a USB key for total security. So what if someone confiscates that key? No problem! You see, the Tails project set up the key in such a way to have a special encrypted directory that holds not just all of your data (browsing info, etc) but anything else you care to store there. Anyone not knowing the pass phrase has no chance to get at your files. Kind of like having your cake and eating it too.
I have used this software a great deal and have noticed the following:
- Tails works so well that often when connecting to mainstream sites through the onion network they often think I am a hacker and put me through additional screening. No problem but just be ready. Linkedin is one site that is hideously bad about it since it thinks that I am logging in from a different place in the world every few hours ;) Still, there are ways around everything.
- One thing that you will want to get to know very well in the safe-browser is the NoScript add-on button. At first it will seem like a total pain since what it does is limits or stops any extra scripts from running that a website may throw at you. This can be good to keep them from getting anything at all on you but some times you need to enable scripting just for a single site to get it to function at all. Your friend and mine LinkedIn is like that. Some sites are so script-heavy that they will not function without them and so you have to find the happy medium between security and functionality. There are ways to deal with that but we will explore this more next time.
- Even though the idea of somehow bouncing your signal all over the planet to hide your tracks is laughable, when using the onion router you are still doing a lot of not just extra routing of your signal but it is being encrypted over and over again. All of this takes time so DO NOT DOWNLOAD BIG FILES over the onion network. It clogs the whole thing up and makes it not work well for everyone. There are other secure ways of getting files that I can show you later but for now, just limit your onion router use to browsing, etc.
- Tails is based on Linux but if you know how to click a mouse and can operate a motor vehicle, you will be fine. What is sly about Tails however is that if you are using your key in public, folks seeing your Linux (UNIX) screen might think that you are up to something. To fix this, Tails built in an option when you first boot it up to use what they call "Windows Camouflage". What this does it re-arranges your screen so it looks like Windows XP in the current tails version and in the next one (I have played with the beta), it looks just like Windows 8. Very cool:
- This may seem obvious to most but you should only use this WMD-level security if you really are needing it. For one thing, it is slower and trickier than normal web browsing simply because of all the extra moving parts. For another, if you use this for all of your browsing you will find that you will sometimes have to do a lot to get some mainstream websites to work. They either end up not working at all or you disable so much of your security that it is almost useless. Thus, for email, shopping, etc, just use your normal connection. When tracking someone or using Social Engineering, you use this and when done, shut it all down.
Until next time! For now I will leave you with a little profile someone did on me once so you can recognize me!
Love and kisses,
Radical Ed..
CWJTechTeam at Gmail dot com




No comments:
Post a Comment